Reconnaissance
Reconnaissance is the gain of information especially through survey.It is also the first stage in hacking. You can collect information from host, network or people involved.
It takes place in two parts :
a) Passive reconnaissance is the gain of information without probing the target system. It’s majorly use of search engines and other platforms such as social media, freelancer.
Main example is google dork i.e intitle:”webcamxp 5″ and attacker can gather more information from its ip address or domain as he/she progresses to attacking.
b) Active reconnaissance where it involves attacker probing interacting with the system to gain information.Kali Linux In Kali Linux tools for active reconnaissance include nmap & zenmap which are popular, matelgo and many more.
Examples of active reconnaissance
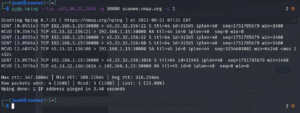
sudo nmap scanme.nmap.org -Pn -sS
syntax : nmap [options] [Scan Type] [target IP/machine]
Option -Pn from above command tells command not to discover host but just start scanning directly.
Option -sS tell nmap to do a SYN Stealth scan , which is only a sync -> ack then it stops, no complete tcp scan.
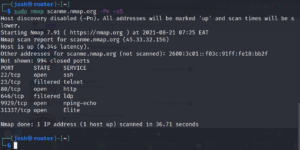
sudo masscan --rate=1000 -p21-1024 scanme.nmap.org
The default way of masscan command is host discover disabled ( -Pn ), SYN Stealth scan only -sS
It also supports integration of nmap scan types and option.
syntax : masscan port[0-65535] [rate (kbs) ] [target-specification]
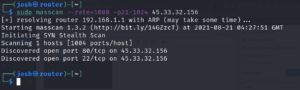
sudo nping --tcp -p21,80,135,22,3036,443,445 1024 -g 30000 scanme.nmap.org
Option --tcp is a probe mode and tell nping to do a tcp probe mode only.
Option -p[number] specifies the port to be scanned if up can be comma separated or range.
Option -g [number] specifies the source port of all the packets being generated.